Protecting Healthcare Data: Why SOC II Compliance Matters in HealthTech Software Implementation

Caroline Mayou
Introduction: Powering the Future with Microsoft’s Power Pages
Microsoft has always been at the forefront, guiding businesses and individuals toward the future. This blog post delves into one of the tech giant’s latest marvels, Microsoft’s innovative portal technology, Power Pages. Portal technology, while not new, has undergone significant transformations, and Power Pages stands as a testament to this evolution. Embedded seamlessly within the broader Microsoft ecosystem, Power Pages is not just another tool; it’s a powerful solution designed to cater to diverse needs.
As we navigate this post, we’ll uncover the manifold advantages of Power Pages, where attributes like scalability, flexibility, integration, security, and cost-efficiency aren’t just buzzwords—they’re foundational pillars. Our journey will take us through various real-world scenarios, showcasing how Power Pages are revolutionizing interfaces, from customer-centric portals and bustling employee intranets to dynamic e-commerce platforms and enlightening educational hubs.
In a world that has witnessed rapid digital shifts post-COVID, the relevance of robust portal technology has never been more pronounced. Power Pages emerge as a beacon for organizations navigating this digital transformation, offering a clear and actionable roadmap for implementation. By the time we reach our conclusion, the transformative potential of Power Pages will be undeniable, prompting you, our esteemed reader, to reimagine its pivotal role in your organization’s digital strategies.
What is Microsoft Power Pages?
In the vast realm of digital platforms and solutions, Microsoft’s ecosystem is akin to an intricate web, where each tool, application, and service complements and enhances the other. One such marvel in this interconnected system is Power Pages.
Build powerful end-to-end business solutions by connecting Power Pages with other Microsoft Power Platform products to drive innovation across your entire organization.
Defining Power Pages Within Microsoft’s Ecosystem
At its essence, Power Pages is Microsoft’s innovative portal technology. Unlike traditional portals that often act as standalone digital gateways, Power Pages is designed to be both a gateway and a bridge. It’s a portal that not only provides access but also seamlessly interlinks various functionalities and data sources, enabling businesses to create bespoke experiences for their users.
But what truly sets Power Pages apart is its deep-rooted integration within Microsoft’s ecosystem. Imagine a puzzle, where each piece, no matter how unique or distinct, fits perfectly. In this analogy, Power Pages is that central piece, around which numerous other Microsoft tools and solutions.
Get to know Power Pages. Learn more about what features and capabilities are now available and how to get started.
Introduction
In an age characterized by remarkable technological strides, the business world is at a crucial juncture. It grapples with the balance between embracing innovation and safeguarding sensitive data. As organizations increasingly turn to technology and data-driven solutions, the stakes have never been higher.
Dynamics 365, the fusion of customer relationship management (CRM) and enterprise resource planning (ERP) in the Microsoft ecosystem, represents a transformative force. From managing customer relationships to optimizing business operations and decision-making, Dynamics 365 solutions promise to redefine the way businesses operate. Yet, amidst this transformative wave, one paramount aspect must remain at the forefront: data security.
This blog post embarks on a journey through the intricate landscape of data security, shedding light on the challenges faced by businesses. We’ll explore the critical link between regulatory compliance, such as SOC II, and Dynamics 365 implementations, revealing how these frameworks work harmoniously to safeguard critical data. Moreover, we’ll delve into real-world case studies that underscore the severe consequences of data breaches in business operations, serving as a stark reminder of the ever-present threats.
But it’s not all challenges and concerns. Our journey also leads us to a reassuring destination – the role of SOC II compliance in Dynamics 365 implementations. SOC II compliance stands as a beacon of assurance, assuring organizations that their data is protected with unwavering diligence throughout the Dynamics 365 implementation process. In the pages that follow, we’ll dissect the pivotal role of SOC II compliant consulting firms in this mission, unraveling the key security measures essential for the success of Dynamics 365 projects. To top it off, we’ll provide valuable insights and tips for selecting the right consulting partner – one equipped not only with SOC II compliance but also with the expertise that Dynamics 365 implementations demand.
So, fasten your seatbelts as we embark on this journey to explore how SOC II compliance plays a critical role in safeguarding data during Dynamics 365 implementations. The future of business operations is dynamic and data-driven, but it must also be secure, and SOC II compliance is the sentinel that ensures it remains so.
Further read: Dynamics 365 Implementation Cost
HIPAA and SOC II Compliance: Understanding the Connection
HIPAA, the Health Insurance Portability and Accountability Act, is a landmark piece of legislation enacted in 1996, designed to safeguard and regulate the use and disclosure of protected health information (PHI). Its overarching goal is to ensure the privacy and security of patient data while facilitating the portability of health insurance coverage. HIPAA consists of several rules, with the Privacy Rule and the Security Rule being of particular importance in the context of data protection.
- Privacy Rule: The Privacy Rule establishes guidelines for how healthcare providers, known as covered entities, may use and disclose PHI. It grants patients rights over their health information, including the right to access and request corrections to their records.
- Security Rule: The Security Rule, on the other hand, sets forth national standards for the security of electronic protected health information (ePHI). It requires covered entities and their business associates to implement safeguards to protect the confidentiality, integrity, and availability of ePHI.
How Soc II Compliance Aligns with and Complements HIPAA Requirements
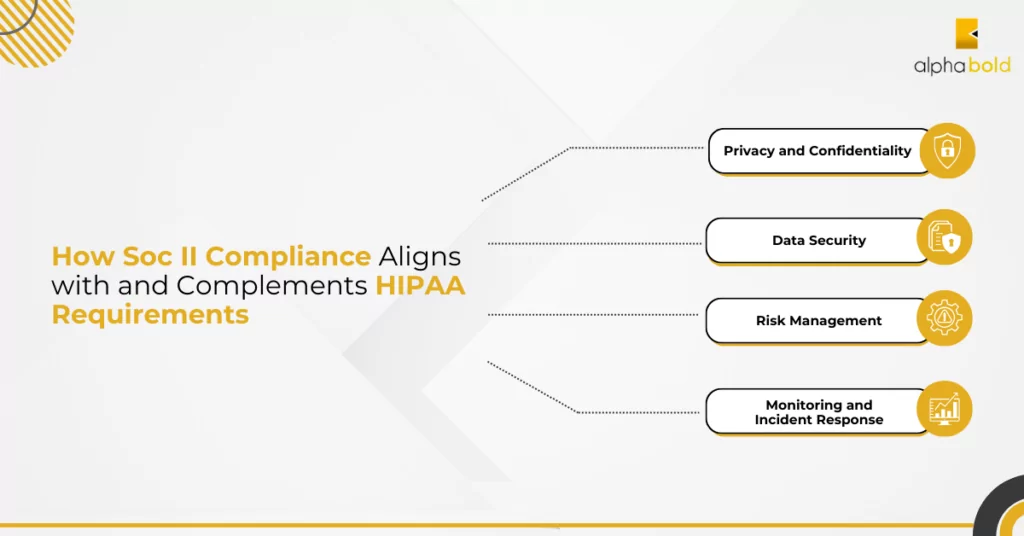
While HIPAA is specific to healthcare and focuses on protecting PHI, SOC II compliance, part of the broader SOC framework developed by the American Institute of CPAs (AICPA), encompasses a broader range of organizations and services. SOC II evaluates the controls in place at service organizations that may impact the security, availability, processing integrity, confidentiality, or privacy of customer data. In essence, SOC II compliance aligns with HIPAA’s objectives in several key ways:
- Privacy and Confidentiality: Both HIPAA and SOC II prioritize the privacy and confidentiality of data. SOC II’s confidentiality principle aligns closely with HIPAA’s Privacy Rule, ensuring that patient data is accessible only to authorized personnel.
- Data Security: The Security Rule of HIPAA and SOC II both emphasize the importance of data security. SOC II compliance requires organizations to implement robust security measures, which often overlap with the Security Rule’s requirements.
- Risk Management: HIPAA and SOC II both necessitate risk assessments and the development of risk management strategies. Regular risk assessments are critical for identifying vulnerabilities and mitigating potential threats to patient data.
- Monitoring and Incident Response: Both frameworks emphasize continuous monitoring and rapid incident response. SOC II’s monitoring and response requirements can help healthcare organizations address security incidents promptly, in line with HIPAA’s breach notification rules.
Benefits of Combining HIPAA and SOC II Compliance in Dynamics 365 Implementations
By combining HIPAA and SOC II compliance in Dynamics 365 project implementations, organizations gain a comprehensive approach to data protection. Here are some key benefits:
- Enhanced Data Security: The dual compliance approach ensures that not only patient data but all sensitive business data is well-protected, reducing the risk of breaches and regulatory penalties.
- Regulatory Confidence: Demonstrating adherence to both HIPAA and SOC II compliance can instill confidence in regulatory bodies and auditors, as well as in patients and customers.
- Streamlined Audits: Combining these compliance frameworks simplifies audit processes, as many controls overlap, reducing the administrative burden of compliance management.
- Competitive Advantage: Organizations that prioritize data security and compliance can use their adherence to HIPAA and SOC II as a competitive advantage, attracting healthcare clients and partners who value robust data protection.
In essence, the connection between HIPAA and SOC II compliance creates a synergistic approach to data security in Dynamics 365 project implementations, fostering a culture of privacy and trust while ensuring the confidentiality and integrity of sensitive information.
Case Studies Showcasing the Impact of Data Breaches in Healthcare
Real-world examples of data breaches and security incidents in healthcare are stark reminders of the vulnerabilities in the industry. These cases underscore the importance of robust data security measures, including SOC II compliance.
Case Study 1: Anthem Inc. (2015)
In 2015, Anthem Inc., one of the largest health insurance providers in the United States, suffered a massive data breach. Hackers gained unauthorized access to the company’s systems, compromising the personal information of nearly 78.8 million individuals. The breach exposed names, addresses, social security numbers, and medical IDs.
Consequences:
- Legal Consequences: Anthem faced multiple class-action lawsuits and investigations by state and federal regulators. The company ultimately settled for a record $115 million.
- Reputational Damage: Anthem’s reputation took a severe hit, with a loss of trust among its members and the broader public.
- Financial Impact: Remediation and recovery efforts cost the company millions of dollars.
Mitigation with SOC II Compliance:
SOC II compliance could have played a pivotal role in mitigating this breach. Specifically, the Security Principle of SOC II focuses on safeguarding sensitive data. Implementing robust access controls, encryption, and monitoring mechanisms, as required by SOC II, could have made it significantly more challenging for hackers to infiltrate Anthem’s systems.
Case Study 2: Cottage Health (2013)
Cottage Health, a California-based healthcare provider, experienced a data breach in 2013 when the medical records of approximately 32,500 patients were exposed due to a configuration error in a server. The exposed data included patient names, addresses, dates of birth, and in some cases, Social Security numbers and medical diagnoses.
Consequences:
- Legal Action: Cottage Health faced legal consequences, including a class-action lawsuit, and eventually settled for $4.1 million.
- Reputation Damage: The breach eroded patient trust and negatively impacted the organization’s reputation.
- Operational Disruption: Remediation efforts and legal proceedings disrupted normal operations.
Mitigation with SOC II Compliance:
SOC II compliance emphasizes the importance of regular vulnerability assessments and controls monitoring. In this case, a comprehensive assessment of server configurations could have identified and rectified the issue before it led to a breach. Additionally, SOC II-compliant incident response procedures could have helped mitigate the impact and legal consequences.
Case Study 3: Hollywood Presbyterian Medical Center (2016)
In 2016, Hollywood Presbyterian Medical Center in Los Angeles fell victim to a ransomware attack. The hospital’s computer systems were encrypted by cybercriminals who demanded a ransom of 40 Bitcoins (equivalent to approximately $17,000 at the time) to unlock the data.
Consequences:
- Financial Loss: The hospital paid the ransom to regain access to its systems, resulting in a direct financial loss.
- Patient Safety Concerns: Patient care was temporarily disrupted, and there were concerns about patient safety.
- Reputation Damage: The incident garnered negative media attention, affecting the hospital’s reputation.
Mitigation with SOC II Compliance:
SOC II compliance’s emphasis on data encryption and regular backups could have played a crucial role in preventing or mitigating this attack. With proper encryption measures in place, the ransomware may not have been able to encrypt sensitive patient data, and with regular backups, the hospital could have quickly restored its systems without paying the ransom.
These case studies underscore the severe consequences of data breaches in healthcare and emphasize the vital role SOC II compliance can play in preventing and mitigating such incidents. By adhering to SOC II’s rigorous security principles, organizations can proactively protect patient data and preserve their reputation in an increasingly data-driven healthcare landscape.
How SOC II Compliant Consulting Firms Can Help Healthcare Companies
Now that we’ve explored the critical importance of data security in Dynamics 365 projects, it’s time to delve into how SOC II compliant consulting firms can be invaluable partners in these endeavors.
The Role of Consulting Firms in Dynamics 365 Software Implementations
Consulting firms play a pivotal role in Dynamics 365 software implementations. They are the architects, guiding organizations through the complex process of planning, configuring, and deploying Dynamics 365 solutions. These firms bring expertise, best practices, and a deep understanding of the Dynamics 365 platform to ensure that the implementation aligns with the organization’s goals and objectives.
The Specific Advantages of Partnering with SOC II Compliant Consultants
When choosing a consulting partner for your HealthTech Dynamics 365 project, opting for a SOC II compliant firm offers several distinct advantages:
- Data Security Expertise: SOC II compliant consulting firms have demonstrated their commitment to data security and privacy. They possess the expertise necessary to design and implement security controls that safeguard your sensitive data, ensuring HIPAA and other regulatory requirements are met.
- Comprehensive Risk Management: SOC II compliance encompasses risk assessment and management practices. These firms are well-versed in identifying vulnerabilities, assessing risks, and implementing mitigation strategies. This proactive approach helps prevent security incidents and data breaches.
- Continuous Monitoring and Improvement: SOC II compliance necessitates ongoing monitoring of security controls. Compliant consulting firms continuously assess and improve security measures, ensuring that your Dynamics 365 environment remains resilient against evolving threats.
- Incident Response Capabilities: In the unfortunate event of a security incident, SOC II compliant consultants have well-defined incident response procedures. Their swift and effective response can minimize the impact of security breaches and help organizations navigate the aftermath efficiently.
Examples of How SOC II Compliance Contributes to Secure Dynamics 365 Implementations
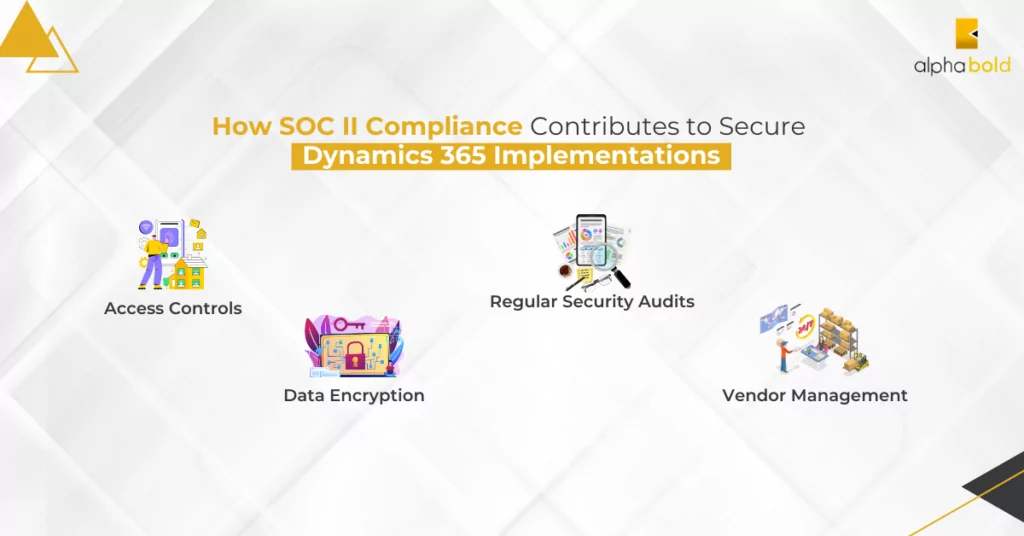
Let’s examine how SOC II compliance translates into tangible benefits for Healthcare companies undertaking Dynamics 365 projects:
- Access Controls: SOC II compliance mandates robust access controls. Consultants ensure that only authorized personnel have access to sensitive data within Dynamics 365. This prevents unauthorized users from tampering with or extracting valuable information.
- Data Encryption: Compliant firms implement data encryption measures within Dynamics 365 to protect data at rest and in transit. This safeguards patient data from interception or theft.
- Regular Security Audits: SOC II compliance requires regular security audits and assessments. These audits identify vulnerabilities and weaknesses in the implementation, enabling proactive fixes before they can be exploited.
- Vendor Management: SOC II compliant consulting firms also assess the security practices of third-party vendors and integrations within the Dynamics 365 ecosystem. This ensures that the entire solution ecosystem maintains the same high standards of security.
In summary, partnering with SOC II compliant consulting firms offers Healthcare companies a strategic advantage in their Dynamics 365 implementations. These firms bring data security expertise, comprehensive risk management, continuous monitoring, and effective incident response capabilities to the table. By aligning with SOC II compliance, organizations can confidently navigate the Healthcare landscape.
Want to fortify your Dynamics 365 projects against security threats and data breaches?
Partner with AlphaBOLD to accelerate towards a more extensive protective environment.
Request ConsultationKey Security Measures Required for Healthcare Software Projects
In the world of healthcare software development, data security is not a mere option; it’s an absolute necessity. Here, we’ll outline the essential security measures and best practices that must be woven into the fabric of every healthcare software project. These measures are critical for safeguarding patient data and ensuring compliance with regulations such as HIPAA.
Detailing Essential Security Measures and Best Practices
- Encryption: Encryption is a fundamental security measure that protects data both at rest and in transit. For healthcare software, sensitive patient information, like medical records and personal details, should be encrypted to thwart unauthorized access, even if a breach were to occur.
- Access Controls: Granular access controls are crucial to limit data access to authorized personnel only. Implement role-based access controls (RBAC) to ensure that users can only view or modify data necessary for their roles. This prevents unauthorized individuals from accessing confidential patient information.
- Data Backup and Recovery: Regularly back up healthcare data to prevent data loss in case of system failures, cyberattacks, or natural disasters. A robust data backup and recovery strategy ensures that patient data remains accessible and intact, even in the face of adversity.
- Incident Response Planning: Prepare for the worst by developing a well-defined incident response plan. This plan outlines the steps to take in the event of a data breach or security incident. It should include procedures for notifying affected parties, containing the breach, and cooperating with regulatory authorities.
- Continuous Monitoring: Continuous monitoring of systems and networks is essential to detect and respond to security threats promptly. Implement intrusion detection systems (IDS) and intrusion prevention systems (IPS) to identify and mitigate threats in real-time.
- Compliance Assessments: Regularly assess your healthcare software project for compliance with relevant regulations, such as HIPAA. Compliance assessments should encompass data security, privacy, and audit trails. Regular audits and assessments help identify and address compliance gaps proactively.
Discussing the Importance of Each Measure
Encryption ensures that even if unauthorized parties gain access to data, they cannot decipher its contents. Access controls prevent unauthorized personnel from viewing or altering patient records, maintaining confidentiality. Data backup and recovery are crucial for ensuring data availability and integrity. In the event of a breach, incident response planning helps minimize damage and legal repercussions. Continuous monitoring safeguards against evolving threats and vulnerabilities. Compliance assessments ensure that your healthcare software project adheres to regulatory standards, mitigating risks associated with non-compliance.
Emphasizing the Need for Continuous Monitoring and Compliance Assessments
Cyber threats are constantly evolving, making continuous monitoring a non-negotiable aspect of healthcare software security. Regular compliance assessments help organizations stay up to date with the latest regulations and security best practices. They also provide insights into areas that require improvement, ensuring that patient data remains secure and the healthcare software project remains compliant over time.
In conclusion, healthcare software projects must incorporate these key security measures and best practices into their development process. By doing so, organizations can protect patient data, maintain compliance with healthcare regulations, and uphold the trust and confidence of patients and stakeholders in an ever-evolving digital healthcare landscape.
Tips for Selecting a Consulting Partner With SOC II Compliance and Healthcare Expertise
Choosing the right consulting partner for your Dynamics 365 project is a critical decision that can significantly impact the success of your initiative. To ensure you make an informed choice, here’s a checklist of criteria to consider when evaluating potential consulting firms.
1. SOC II Compliance and Healthcare Expertise
- Verify SOC II Compliance: Ensure the consulting firm is SOC II compliant, particularly in the relevant trust service categories (e.g., security, confidentiality, and privacy). Request their SOC II report to assess their adherence to data security standards.
- Healthcare Domain Knowledge: Evaluate the firm’s healthcare industry expertise. Look for consultants who understand the unique challenges, regulations, and intricacies of Dynamics 365 projects.
2. Track Record and References
- Client References: Request and contact references from previous clients, particularly those in the healthcare sector. Inquire about the firm’s performance, adherence to deadlines, and the overall quality of their work.
- Case Studies: Review case studies or success stories related to previous Dynamics 365 projects. These can provide insights into the firm’s capabilities and achievements.
3. Certifications and Credentials
- Certified Professionals: Ensure that the consulting firm employs certified professionals, such as Microsoft Certified Dynamics 365 consultants, who possess the expertise required for your project.
- Relevant Certifications: Check if the firm holds certifications relevant to your project, including HIPAA compliance certifications or any specific Microsoft-related certifications.
4. Security Practices
- Data Security Measures: Inquire about the consulting firm’s data security practices beyond SOC II compliance. Ask about their encryption standards, access controls, and incident response procedures.
- Security Audits: Check if the firm conducts regular security audits and assessments to proactively identify and address vulnerabilities.
5. Project Methodology and Approach
- Data Security Measures: Inquire about the consulting firm’s data security practices beyond SOC II compliance. Ask about their encryption standards, access controls, and incident response procedures.
- Security Audits: Check if the firm conducts regular security audits and assessments to proactively identify and address vulnerabilities.
6. Communication and Collaboration
- Communication Skills: Evaluate the firm’s communication skills and responsiveness. Effective communication is essential for project success and client satisfaction.
- Collaborative Approach: Determine if the firm promotes a collaborative working relationship, fostering a partnership rather than just a vendor-client dynamic.
7. Scalability and Resources
- Resource Availability: Ensure the firm has the necessary resources, including skilled consultants and technical expertise, to handle the size and complexity of your Dynamics 365 project.
- Scalability: Consider whether the firm can scale its services if your project grows or evolves.
8. Project Management and Documentation
- Project Management Expertise: Assess their project management capabilities. A well-structured project management approach is crucial for keeping projects on track.
- Documentation: Confirm that the firm maintains detailed project documentation, including requirements, design, and testing records.
By carefully evaluating consulting firms against these criteria, you can make an informed decision that aligns with your Dynamics 365 project’s unique needs.
Further read: “How to Choose a Dynamics 365 Customer Engagement Partner for Your Business – Why”
Conclusion
In the ever-evolving landscape of healthcare software implementation, data security stands as an unwavering pillar of trust, one that patients, healthcare providers, and organizations rely upon. This journey through the importance of SOC II compliance in the Healthcare industry’s software implementation has illuminated key insights and critical considerations that deserve your attention.
Key Takeaways
- Data Security is Paramount: The healthcare industry is entrusted with some of the most sensitive and confidential data. Protecting patient information is not only a legal requirement but also an ethical obligation.
- HIPAA and SOC II: HIPAA sets the regulatory framework for healthcare data protection, while SOC II compliance provides a comprehensive approach to security controls that align harmoniously with HIPAA requirements.
- Real-World Consequences: Real-world data breaches in healthcare serve as stark reminders of the damage that security incidents can cause, including legal ramifications, reputational harm, and financial losses.
- The Role of SOC II Compliant Consulting Firms: Consulting firms play a pivotal role in Healthcare software implementation, guiding organizations through the intricacies of the process. When these firms are SOC II compliant, they bring a higher level of data security assurance to the table.
- Key Security Measures: Encryption, access controls, data backup, incident response planning, continuous monitoring, and compliance assessments are essential components of a robust security posture for healthcare software projects.
- Choosing the Right Partner: When selecting a consulting partner for Dynamics 365 projects, look for SOC II compliance, healthcare domain knowledge, a proven track record, relevant certifications, robust security practices, effective communication, and scalability.
SOC II compliance is not just a checkbox; it’s a commitment to data security excellence. It forms a protective shield around your patients’ information, ensuring their privacy and trust are upheld. The compliance framework’s holistic approach to security aligns seamlessly with the stringent requirements of the healthcare industry, making it a natural choice for safeguarding critical data.
Ready to combine SOC II compliance with healthcare expertise?
AlphaBOLD ensures a robust foundation for data security and project success in the dynamic world of healthcare.
Request ConsultationPrioritizing Data Security and Wise Partner Selection
As the custodians of patient data, Healthcare companies bear a profound responsibility. Prioritizing data security is not only a regulatory obligation but also a commitment to patient well-being. It’s a promise to protect what matters most.
In the world of Healthcare software implementation, your choice of consulting partner is pivotal. SOC II compliance is a badge of honor that signifies a firm’s dedication to safeguarding your data. When you choose a consulting partner wisely—considering their expertise, compliance, and commitment to security—you strengthen your position as a trusted steward of patient information.
In closing, remember that data security is not an option; it’s a fundamental requirement. As you embark on your Dynamics 365 journey, embrace SOC II compliance as your ally, and forge partnerships with those who share your unwavering commitment to preserving the sanctity of healthcare data. In doing so, you not only protect your patients but also ensure the future of healthcare remains secure and resilient in the digital age.
Explore Recent Blog Posts







