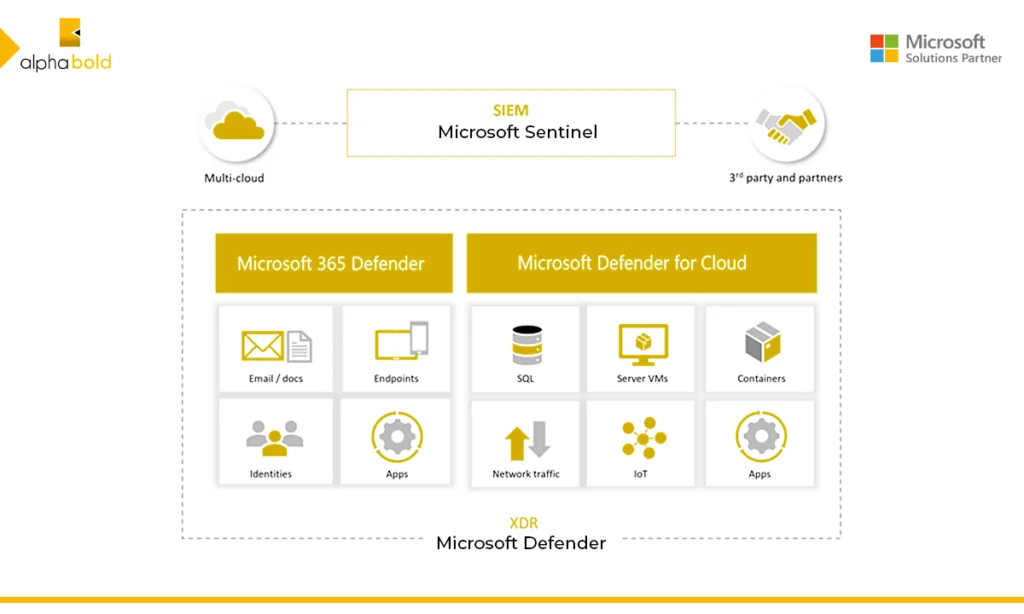
Introduction
In this digital odyssey, where attackers, hackers, and overall cyber threats loom larger than ever, Microsoft Sentinel can be your vigilant guardian and a watchful protector—blended with the prowess of SIEM (Security Information and Event Management) and the spryness and agility of SOAR (Security Orchestration, Automation, and Response). According to Forbes, as of May 2023, over 2.5 quintillion bytes of data are created and ingested worldwide.
In this blog, we’re diving deep into the large spread of cyber seas, navigating through the waves of information, and exploring the big fish of insights. By the end of this blog, you’ll come to know that you are not just monitoring your huge chunks of data and keeping checks on it with Microsoft Sentinel, but you are also setting sail on the most advanced vessel in the cybersecurity fleet, equipped and armed with the intelligence to outsmart the threats, and how Microsoft Sentinel is rewriting the rulebook of digital security, one byte at a time!
Key Features of Microsoft Sentinel
Microsoft Sentinel stands as a beacon of innovation in the realm of cyber security. The core strength of Microsoft Sentinel lies in its seamless integration of SIEM and SOAR functionalities, providing a comprehensive solution that not only detects anomalies and threats but also reduces the noise of unwanted alerts. Gone are the days when SOC analysts had to sit through an overwhelming flood of alerts. Instead, with Sentinel, you can create custom rules to ingest the alerts from the data sources you wish to collect data and insights from.
Sentinel employs advanced data analytics, powered with AI , to sift through the digital noise, identifying and isolating the threats that require attention with precision. This means that security teams and SOC analysts can focus on what truly matters, responding to alerts and incidents accurately and precisely. Sentinel is a cloud-native solution that ensures scalability with its ability to integrate with both Microsoft and non-Microsoft data Sources, allowing it to be adept and adapt to the ever-evolving landscape of threats for an organization.
With Sentinel’s advanced hunting and threat detection capabilities, you can proactively hunt threats before they happen. With Microsoft Sentinel’s sophisticated threat-hunting capabilities, analysts can delve into the depths of their organization, analyze the historical data of threats, build a wall to keep the data within the organization safe from such threats in the future, and provide a 360-degree view of the security landscape. With comprehensive visibility, intuitive tools and dashboards, and ingesting raw data into one solution for actionable intelligence, Sentinel’s proactive stance on threat hunting bolsters defense and fosters a culture of vigilance, keeping organizations one step ahead in cybersecurity. With automation rules and playbooks in Sentinel, you can automate the remediations your SOC analysts spend time on daily or weekly, making them more concentrated on the threats that need attention.
Onboarding Microsoft Sentinel:
Microsoft Sentinel is just like any other solution that can be installed in your Microsoft environment. The prerequisites for onboarding Microsoft Sentinel into your environment include the following:
- Active Azure Subscription to build your solution.
- Log Analytics Workspace is the core foundation of Microsoft Sentinel. The entire Microsoft Sentinel solution is built on top of just a Log Analytics Workspace in Azure.
- Appropriate permissions (at least contributor) to the subscription your Microsoft Sentinel solution is going to reside in. Apart from that, you might also need the role of Microsoft Sentinel Contributor on the resource group to which the workspace belongs.
Further read 4 Reasons to Start Using Azure ML Studio for more insights.
Enabling Microsoft Sentinel:
The core steps involved in enabling the Microsoft Sentinel solution in your environment are as follows:
- Add Microsoft Sentinel to Log Analytics Workspace.
- Installation of data collection solution from content hub.
- Setting up the data connector.
- Enabling the data connector to start generating activity data.
- View and analyze ingested data and information with Workbooks or Log Analytics queries.
Secure your Future with Microsoft!
Embrace a secure, innovative future. Explore how Microsoft's solutions can protect and propel your business forward.
Request a ConsultationData Collection and Management:
Focusing on a diverse array of security-related information, the data collection in Microsoft Sentinel is a comprehensive challenge, and the system is designed to accumulate huge chunks of logs and other relevant data into the Microsoft Sentinel Workspace. This extensive data gathering is enabled through various Microsoft and non-Microsoft solutions connectors. The data is collected and stored securely in Azure Log Analytics Workspace, thus providing a unified data repository where you can use multiple log analytics queries to play around with the data and extract the results, analytics, and insights of your choice. Sentinel also employs advanced analytics, including Machine Learning Algorithms, which we can use further in the Notebooks feature within Sentinel to obtain advanced analytics and configure proactive hunting.
The robust data collection and management within Sentinel are pivotal in empowering the organizations. The SOC analysts should proactively identify threats and remediate them effectively.
Collection of Data within Sentinel:
To onboard Microsoft Sentinel, you must connect the data sources to ingest alerts and activity in Sentinel. Microsoft Sentinel has several data connectors or sources for Microsoft and non-Microsoft solutions. It includes out-of-the-box solutions and provides real-time integration with
- Microsoft data sources from Microsoft Defender XDR to Azure Key Vault and more.
- Microsoft Sentinel also comes with built-in connectors for non-Microsoft solutions, and you can use those connectors for your ecosystem. In addition to these, you can use CEF or Common Event Format, Syslog, or REST-API for broader security and connect your data sources with Microsoft Sentinel.
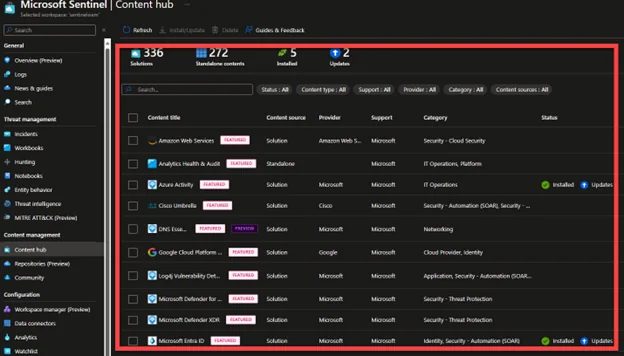
Visualization of Data
The overview dashboard is handy to get a bird’s eye view of data and overall insights in Microsoft Sentinel. You can get an idea of the overall analytics from the default dashboard, and you can view incident data, automation data, and the statuses of data records, data collectors, and threat intelligence. Workbooks are another more versatile, detailed, and customizable feature available in Sentinel.
What are Workbooks?
Workbooks provide SOC analysts with integrated data from the already connected data sources, which lets you customize the layout and enables you to dive deep into the events and data gathered and generated from those services. Workbooks collect all kinds of data, such as events from Windows Servers, third-party alerts, firewall traffic logs, insecure protocols, etc. Workbooks are only Azure Monitor Workbooks, allowing you to customize them according to your security needs.
When you have connected your data sources to Microsoft Sentinel, you can visualize and monitor the data coming from those connectors using the workbooks that come along with those connectors as packaged solutions. You can also utilize the capabilities of Microsoft Power BI to visualize your data and create visually appealing reports.
Discover how Power BI data visualization capabilities can benefit high growth companies like yours. Further insights are available here: Handling Big Data: Performance and Limits of Power BI.
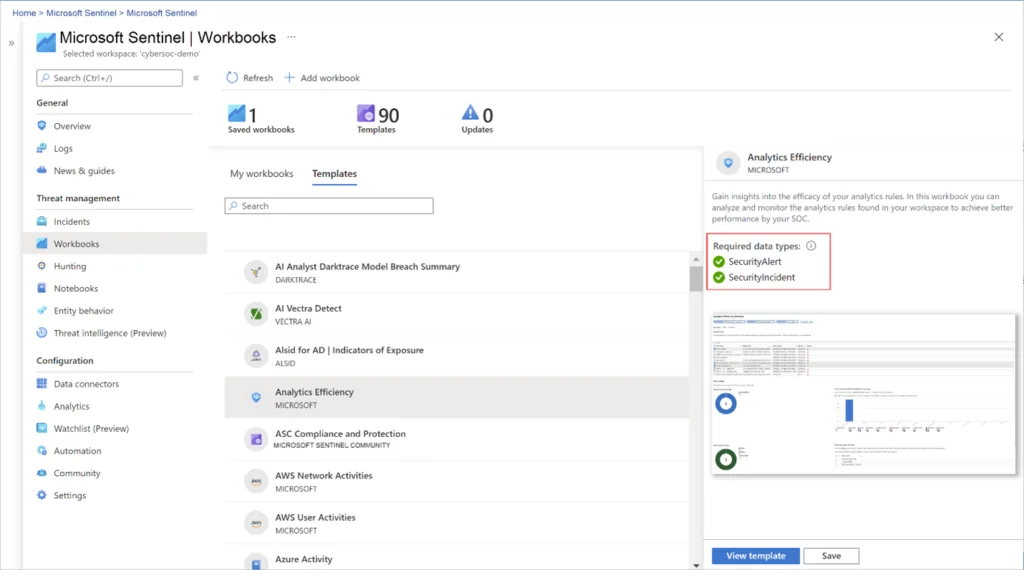
Real-Time Analytics, Detection and Advanced Threat Hunting
Microsoft Sentinel collects logs, data, and alerts from all its data sources and analyzes and builds behavioral profiles of your organization. Using various techniques and enhanced capabilities, Sentinel flags identify and help you remediate any anomalous and suspicious activity to identify further if the entity has been compromised. Sentinel’s Security-driven analytics help the SOC analysts get a broader view and better understand unusual activities with the baseline security and profiles.
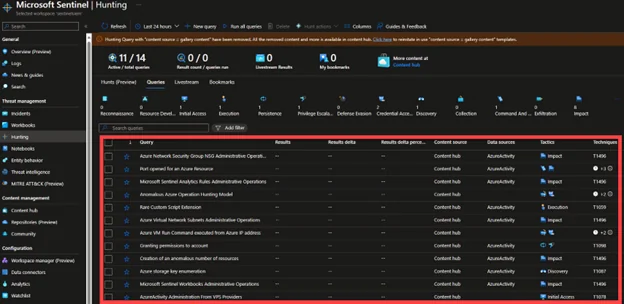
Hunt proactively with Hunting Queries:
In Sentinel, you can use Hunting queries and exploration queries to proactively hunt for any threats before they happen, and which remain undetected by the security applications or already configured analytics rules. It is always difficult to parse and filter meaningful events from an ocean of events, and incidents and can be a toll on your security analysts. This is where hunting queries come in, which can give you an entry point to parse and look for new threats that go undetected and help you figure out where to start hunting for new attacks. You can use hunting queries for a series of actions to help you in tackling any compromise that happens in your environment.
In addition to the already available hunting queries in Sentinel workspace, you can also create your custom queries, and parse through the tables depending on your needs of the organization. Bookmark the items or results that look suspicious to you during hunting and investigation process, and you can refer to these items in future if a similar event occurs again.
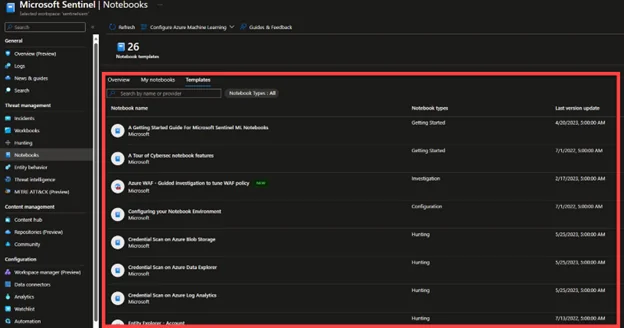
Use the Power of Notebooks:
In addition to the already available powerful features of Sentinel, you can also empower your findings, investigations and hunts using Microsoft Sentinel notebooks to enhance the investigation activity with machine learning, and data analysis. Notebooks provide you a virtualized isolated environment where you can run your tests, use the raw data, and get its visualizations.
Notebooks are Jupyter Notebooks, which is an open-source, and interactive development environment and integrated directly with your Sentinel Workspace. You can utilize Jupyter Notebooks with the Python capabilities of pandas, Matplotlib, NumPy, scikit-learn, TensorFlow and Keras for data visualization, scientific processing, and deep learning respectively.
Unleash the hidden power of Analytics Rules:
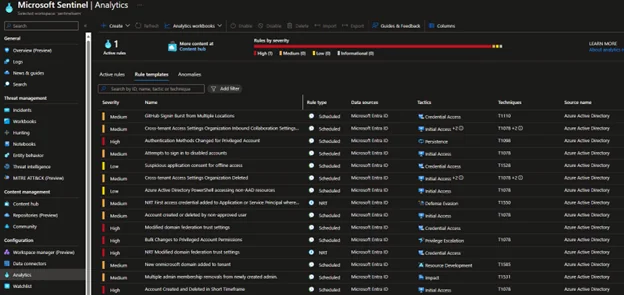
Create scheduled analytics rules to dig through all the data to detect security incidents from your environment. The pre-designed analytics rules are customizable, and you can create your own to help you create detection rules to do the work. These rules sweep across your environment and search for suspicious activity. A whole bunch of rule types in Sentinel help you in threat detection. These include:
- Microsoft Security
- Fusion
- Machine Learning Behavioral Analytics
- Threat Intelligence (TI)
- Anomaly
- Scheduled
- Near-real-time (NRT) Rules
You should always enable all rules associated with the data solutions with Microsoft Sentinel to ensure full security coverage, and this is the most efficient way to reduce the management overhead of looking for millions of events ingested in Microsoft Sentinel daily.
You can also use rules in Microsoft Sentinel via API and PowerShell, which require exporting to JSON first before enabling the rules.
Unleash the Power of Microsoft Sentinel
Discover how Microsoft Sentinel can be the cornerstone of your security strategy. Learn more about Microsoft’s business solutions with AlphaBOLD!
Request a ConsultationIncident Response and Management:
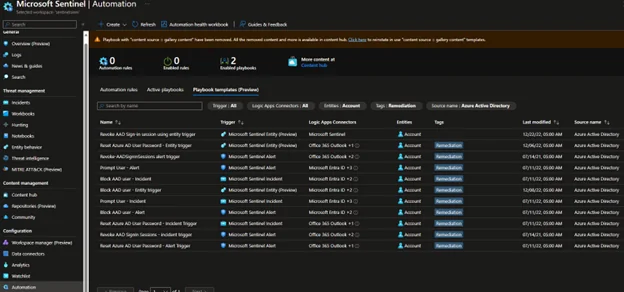
Incident response is a crucial step for any organization that wants to strengthen its security posture and eliminate any threats before, as they happen, and after they happen to keep the entities safe and reduce the overall compromise level. Using the automated workflows that streamline and standardize the response to specific types of alerts, an organization can automate the usual tasks that its SOC analysts perform on a daily or weekly basis to reduce management overhead, help them focus on the events and threats that really matter, and swiftly identify, investigate, and remediate the threats. Fortunately, it is also taken care of by Microsoft Sentinel, where you can use Automation Rules and Playbooks to create automated workflows.
Threat Response Automation with Automation Rules:
Automation rules help you centrally manage automation in Microsoft Sentinel through a set of defined rules to apply in different scenarios. The scenarios include suppressing noisy incidents, triaging new incidents, closing resolved incidents, and controlling the order of actions. The main components that make up the core of automation rules are:
- Triggers define the incident which will cause the rule to run.
- Triggers can either be Incident-based or alert-based, where the former is the most preferred approach with all relevant evidence for a specific investigation.
- Conditions that determine the scenarios under which the rule will run.
- Actions to take on those incidents and alerts.
The order of automation rules is crucial, and you should only set the sequence of automation rules you want them to run because rules always run in sequential order, not in parallel.
Everyday use cases of analytics rules include the standardization and formalization of steps for triaging, investigating, and remediating the incidents, automatic assignment of incidents, suppression of incidents, and automatic tagging of incidents.
Automation with Playbooks
The automated workflows, Playbooks, can be customized using Azure Logic Apps and provide a flexible, robust automation strategy. You can execute various actions, from sending notifications and creating tickets to orchestrating complex remediation steps across the integrated tools and services. Playbooks can really do in milliseconds what it takes for an analyst to do in minutes if not hours. As SOC analysts, you are inundated with security alerts and incidents at overwhelmingly large volumes, which may land you in situations where any crucial incident gets ignored without being investigated in an ocean of less meaningful alerts and leaves the organization vulnerable to undetected threats.
Most of the alerts and incidents follow a recurring pattern and can be addressed using specific remediation actions and activities. Playbooks are just a collection of the remediation actions that run from Microsoft Sentinel on a prescheduled basis and help the analysts automate and orchestrate the threat response. These playbooks are based on Azure Logic Apps workflows, which help schedule and automate the workflows throughout the systems.
Playbooks offer several use cases and scenarios they can be used in, but a good starting point can be using them in any of the following scenarios.
- Enrichment by collecting data and associating it to the incidents to do automated remediations.
- To sync your Microsoft Sentinel incidents with the ticketing systems, thus configuring a Bi-directional sync.
- Immediate response to threats with as minimum human dependencies and interactions as possible.
Leveraging Microsoft Defender XDR for Endpoint with Sentinel
Microsoft Defender XDR’s incident integration allows the analysts to ingest all Microsoft Defender XDR incidents to Microsoft Sentinel and keeps them synchronized and updated between both portals. Microsoft Defender XDR incidents include all kinds of alerts, entities, and information related to those entities and incidents, and once these incidents appear in Sentinel, they remain bi-directionally synced with Sentinel. This integration reduces the management overhead of managing two platforms and portals for efficient incident management, and you can maintain one queue for all kinds of alerts, incidents, and remediation actions.
You can still leverage both platforms’ strengths and capabilities while reducing the time required to resolve incidents. The incidents from Defender XDR will appear in the Sentinel queue with details like any other incidents in Sentinel. The incidents evolve in the Sentinel just as they do in Defender XDR.
Best Practices for Microsoft Sentinel
1. Design of Architecture:
While designing your Sentinel workspace architecture, walk through the decision tree provided by Microsoft to configure your overall security architecture in Sentinel efficiently. Choose only the effective data sources and the solutions you seek to extract the most valuable insights. Assign only the required permissions to analysts in your organization because Sentinel uses Azure RBAC and find out whether all or some users need access to the tables and rows in Sentinel.
Costs in Sentinel are of the utmost importance regarding large data ingestion rates. The ingestion rate is usually in GB/day and should be one of the key considerations while planning Sentinel workspace architecture.
Segregate the data and define the boundaries of ownership, and if you want one or multiple instances of workspaces in Sentinel. Control the access by data sources and on granular levels, even on tables.
2. Integration with Solutions of Environment:
Sentinel’s arsenal is equipped with loads of data sources and solutions that send data to the workspace, and only through integration does Sentinel get stronger. All kinds of log activities from those data sources get ingested into Sentinel. You can leverage analytics rules to filter them out, configure playbooks, and automation rules to investigate and remediate all those logs and flag any suspicious activities.
The best example is to use products such as in Sentinel to get all logs from these services to create incidents and detections in Sentinel.
3. Use Hunting Queries to Always Be One Step Ahead:
Leverage hunting queries to maximize intelligence-based detections and intelligent threat hunting. This approach reduces the compromise rate in your environment over time and strengthens your overall security posture. Using a watchlist helps you enrich your data.
Dive further into the Azure landscape by exploring AlphaBOLD’s Azure DevOps services.
Upgrade your Security Posture with Microsoft Sentinel!
Partner with AlphaBOLD to navigate the present cybersecurity challenges and pain points. Together, we can tailor Microsoft's business solutions to fortify your defenses and drive strategic growth.
Request a ConsultationConclusion
In conclusion, Microsoft Sentinel stands out as a powerful and adaptable tool in cloud native SIEM (Security Information and Event Management) solutions. Its ability to seamlessly integrate with a wide range of data sources and its advanced analytics and threat detection capabilities make it a highly effective tool for organizations looking to enhance their security posture. Sentinel’s user-friendly interface and flexible scalability cater to small businesses and large enterprises, ensuring that organizations of all sizes can effectively monitor, analyze, and respond to security threats. As cyber threats evolve, Microsoft Sentinel provides a robust, proactive approach to security, empowering organizations to stay ahead of potential risks and safeguard their digital environments.
Explore Recent Blog Posts








