Introduction
This blog post will explore how Azure offers the privacy, security, and compliance that your company requires for growth and scalability. Moreover, it will offer a comprehensive section on the best practices for Microsoft Azure Identity and security for growth.
Several companies are embracing the flexibility and scalability of cloud computing. However, this change poses an important question: How can access control and data security be maintained without impeding growth?
If your business is based on cloud computing, you must stay vigilant and prioritize data and application security. Because let’s be honest- cloud security is not a walk in the park; it’s a complex process, and one of the biggest challenges is to ensure that the right people have access to classified and restricted information.
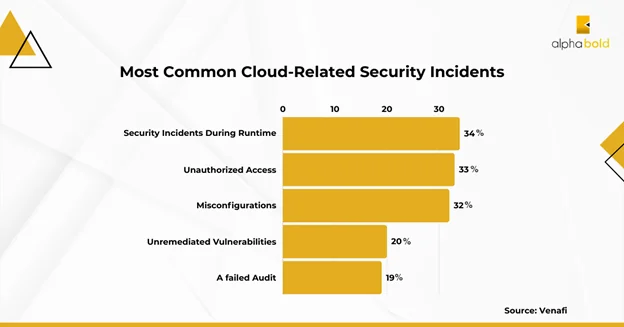
With advanced tech easily accessible and cybercrimes at an all-time high, 70% of companies are not confident about their security measures across multi-cloud environments. Moreover, 83% of organizations have reported at least one data breach on their cloud, with 50% of these issues directly related to access permission issues.
This is where Microsoft Azure’s Identity and Security Management, a critical factor of Azure cloud computing, will save you. Microsoft Azure is built around key concepts like information security, privacy, compliance, and disaster recovery.
Microsoft invests $1 billion annually in security research and development, employing about 3,500 security specialists. You cannot compete with it as a company running on-premises. Microsoft’s comprehensive identity and access management (IAM) service, Azure Active Directory (Azure AD), offers a strong, scalable, and secure way to manage and safeguard user identities and resource access.
The Significance of Identity and Security in Cloud Growth
With technology advancing exponentially, companies are using cutting-edge solutions to stay true to industry standards and provide the best possible user experience combined with strong security. The notion of identity management has been gaining a lot of traction in the sphere of consumer information security as the frequency of data breaches rises sharply.
Identity management, however, offers considerably more protection than only safeguarding private customer information and confidential company data. Decision-makers and global leaders employ consumer identity and access management (CIAM) to balance security, convenience, scalability, and user experience to accelerate corporate growth.
Let’s dig a little deeper into how a supercharged identity management solution will provide a good foundation for your business’s growth and scalability.
- Saving time and resources with authentication and access management: It goes without saying that the most important investments for any firm are time and resources, which can increase overall productivity and earnings when used wisely. If an organization attempts to handle certain security threats across many platforms and devices without depending on a centralized approach, it will waste resources, and put other investments at risk. Therefore, it is unquestionably necessary to have a single solution that enables you to maintain data security and regulate access, such as Azure’s Active Directory.
Suggested read: Resources Deployment by Azure Resource Manager.
- Scalability and digital transformation: Peak loads can significantly impair performance and negatively impact the user experience if there isn’t a sufficiently scalable infrastructure to manage the growing number of account setups and logins. This could force your prospective clients to move on immediately because everyone is searching for the best user experience from the start. A strong identity management system, like Azure’s, could be the difference between success and failure, particularly when the precise scope of the system requirement is uncertain.
Microsoft Azure identity and security solutions allow you to grow together with your business to quickly scale up your operations and adjust to the constantly evolving digital world. By combining identity management and security with Azure’s powerful capabilities, companies can efficiently tackle the security challenges of the digital era.
Bonus read: Setup Azure AD with ADFS as Dynamics on-prem IDP.
Overview of Microsoft Azure Identity and Security Services
Any business or IT manager would prefer peace of mind, and Microsoft Azure offers security for businesses of all sizes, protecting their data and apps. Here’s how Azure makes sure your company stays out of the reach of security threats lurking on the cloud:
- Multi-layered security: Azure uses defenses like the Azure Firewall, Azure Security Center, and Azure Sentinel as part of its multi-layered security strategy. This all-encompassing security approach provides thorough protection for your whole cloud system.
- Data encryption: Azure uses data encryption both in transit and at rest to protect your private data from prying eyes.
- Adherence to industry-specific compliance standards: FedRAMP, GDPR, and HIPAA are just a few of the regulations that Microsoft Azure complies with. Azure enables your company to fulfill its regulatory requirements by adhering to these standards.
- Identity and Access Management: To guard your company’s apps and data from illegal access and any breaches, Azure uses advanced identity management solutions like Azure Active Directory and Multi-Factor Authentication.
Achieve the Utmost Level of Security with Microsoft Azure’s Active Directory!
With our expertise in Microsoft Azure access management services, we can assist you in configuring an Azure Identity and access management solution that works for your company. Want to see how? Get in touch with our Azure experts!
Request a DemoBest Practices for Implementing Microsoft Azure Identity and Security Management
The section will provide a general roadmap to a more robust security posture after the deployment of your Microsoft Azure identity and security infrastructure. Opinions and technologies change over time and this article reflects the latest tips and best practices through Microsoft Learn. Let’s get right into it:
The following are recommended practices for managing identities in Microsoft Azure Active Directory for access management:
1. Make Identity Your Primary Security Perimeter:
Identification serves as the main security perimeter for many organizations. This diverges from the conventional emphasis on network security. The increasing permeability of network perimeters means that perimeter security strategies are no longer as effective as they were before the development of cloud applications.
Azure’s identity and access management solution is Microsoft Entra ID. The cloud-based database and identity management solution Microsoft Entra ID is available to many customers. It is a single solution that integrates identity protection, application control, access management, and core directory services.
Best practice: Focus security controls and detections around the identities of users and services.
2. Centralize Identity Management:
Microsoft recommends you combine your on-premises and cloud databases in a hybrid identity solution. No matter where an account is generated, integration lets your IT staff monitor accounts from one place. Integration also increases productivity by giving your users a single identity to access both cloud and on-premises resources.
Best practice:
- Create one Microsoft Entra deployment of the IAM service for your organization. This will help lowering security concerns from human errors and one reliable source will improve clarity and reliability in complicated configuration.
- Integrate Microsoft Entra ID with your on-premises databases.
3. Manage Connected Tenants:
To evaluate risk and assess compliance with organizational rules and any applicable regulations, your security team needs visibility. Ensure every subscription linked to your production environment and network is visible to your security organization. In Microsoft Entra ID, a global administrator can boost their access to user access.
Best practice: Log in as an administrator to view all managed groups and subscriptions associated with your environment.
4. Enable Single Sign-On:
Enabling single sign-on (SSO) to devices, applications, and services from anywhere is important in today’s mobile-first, cloud-first environment so your users can be productive at all times. Managing different identification systems presents administrative challenges for IT and users who need to keep track of several passwords.
SSO may be accomplished by utilizing a single identity solution across all of your apps and resources. Additionally, whether the resources are in the cloud or on-premises, your users may log in and access them using the same set of credentials.
5. Turn On Conditional Access:
Users can connect to your company’s resources from anywhere at any time using a range of devices and applications. As an IT administrator, you must ensure that these devices adhere to your security and compliance requirements. It is no longer enough to only concentrate on who has access to a resource.
Before deciding on access control, you must consider how a resource can be accessed to strike a balance between security and productivity. This need may be met using Microsoft Entra Conditional Access. You may automate access control choices using Conditional Access by using it to set requirements for cloud app access.
Best practice:
- Control and oversee who has access to company resources.
- Block outdated authentication methods.
6. Plan for Routine Security Improvements:
Since security policies are always changing, it’s critical to include a mechanism in your identity management and cloud framework for you to periodically demonstrate your progress and find new methods for keeping your environment safe.
Microsoft offers a set of suggested security measures called Identity Secure Score, which provides a numerical rating to help you plan future security enhancements and objectively assess your security posture. Additionally, you can see how your score stacks up against others in similar businesses and track your personal trends over time.
Best practice: Make regular security assessments and enhancements based on industry best practices.
7. Enable Password Management:
Using the proper security policies is crucial to preventing misuse if you have several tenants or wish to allow users to change their own passwords.
Best practice:
- Configure your users’ self-service password reset (SSPR).
- Check to see if or how SSPR is actually being used.
- Expand password policies from the cloud to your on-premises systems.
8. Enforce Multifactor Verification for Users:
Microsoft Azure identity and security experts recommend that you implement two-step verification for every user. This covers administrators and other staff members who, if their account is hacked, might have a big influence (such as finance officers).
There are several ways to implement two-step verification. The Microsoft Entra edition you’re using, your licensing program, and your goals will all determine which choice is ideal for you.
The advantages and choices for allowing two-step verification are as follows:
Option 1: Use Microsoft Entra Security Defaults to set up MFA for all users and login techniques. With the help of this solution, you may swiftly and simply impose MFA for all users within your environment while maintaining strict regulations.
Option 2: Modify user state to enable multifactor authentication. By using this strategy, users override Conditional Access restrictions and must complete two-step verification each time they log in.
Option 3: Use a Conditional Access policy to enable multifactor authentication. With this option, you may use Conditional Access to ask for two-step verification in certain situations. Users can log in under certain circumstances if they utilize programs, you deem risky, untrusted devices, or different locations.
Option 4: Assess risk-based Conditional Access policies and use them to enable multifactor authentication.
9. Use Role-Based Access Control:
Any business that uses the cloud must have access control for its cloud resources. Azure role-based access control, also known as Azure RBAC, facilitates the management of Azure resource access, including who can access what areas and how.
Assigning roles or groups to certain tasks in Azure reduces confusion, lowering the possibility of human and automated errors compromising security. Organizations that wish to implement security rules for data access must restrict access based on the principles of ‘least privilege’ and ‘need to know’ security principles.
Best practice: Divide tasks among team members and only provide the access they require to do their jobs. Limit the actions allowed at a certain scope in your Azure subscription or resources rather than granting everyone unlimited access.
Getting Started with Microsoft Azure Identity and Security Management with AlphaBOLD
AlphaBOLD provides a single solution that encompasses all of your Azure requirements, including agile planning, build, testing, release automation, source code control, package management, identity management, continuous integration, testing, and application delivery. Our managed Azure DevOps services consist of:
- DevOps adoption
- Configuration management
- Microservices and infrastructure as code
- Microsoft Azure identity and security management
- Continuous integration (CI) and continuous delivery (CD)
We can help you increase your Azure security and privacy capabilities by a good margin, so you are not one of that 70% of companies that are unconfident about their security capabilities across multi-cloud environments.
Benefit From Our Experience with Microsoft Azure!
We are prepared to assist you! Our BOLDEnthusiasts have assisted several clients with their Azure Service needs. Request a demo and allow us to show you what difference we can make!
Request a DemoConclusion
Since Azure’s identity solutions are designed to expand with your organization, you can easily adapt to the rapidly changing digital landscape and scale up your operations. Through the integration of Azure’s robust technologies with identity management and security, enterprises can effectively address the problems posed by the digital world. This ensures your company keeps expanding and maintaining that crucial advantage over the competition. This way you don’t just keep up but also stay ahead of the curve in the technology market.
Explore Recent Blog Posts